HIPAA Compliance Checklist

This HIPAA compliance checklist what you need to know about HIPAA regulations:
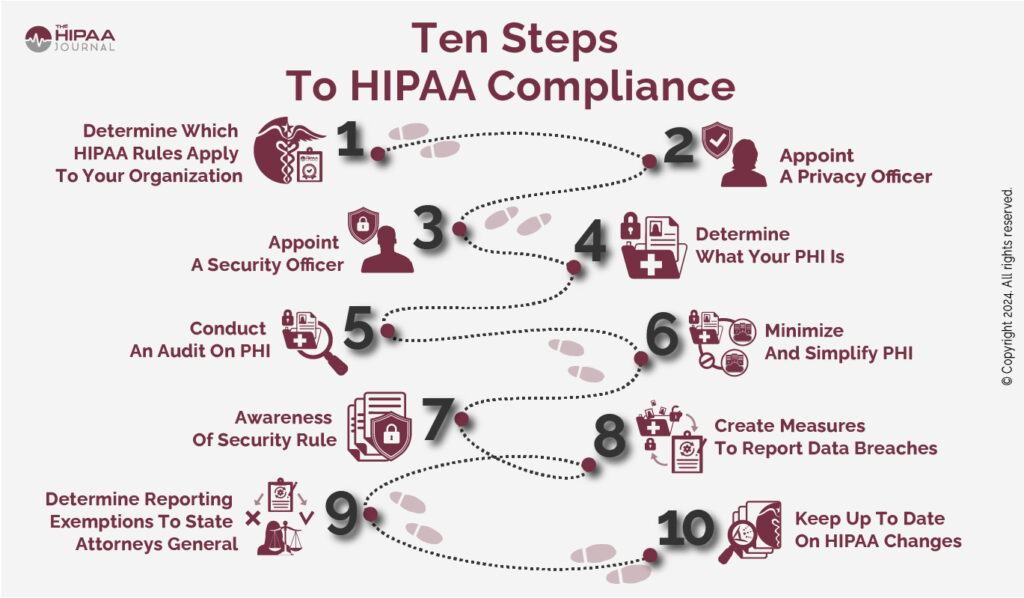
- Establish whether your organization is required to comply with HIPAA.
- Appoint a HIPAA Privacy Officer.
- If required, appoint a Security Officer.
- Understand what PHI is.
- Conduct an audit to determine where how PHI is used.
- Minimize the number of designated record sets in which PHI is maintained.
- Be aware that the Security Rule consists of more than just the Administrative, Physical, and Technical Safeguards.
- Have procedures for notifying individuals and HHS’ Office for Civil Rights of data breaches.
- Verify if your organization is exempted from reporting data breaches to the State Attorneys General.
- Track changes to HIPAA and temporary Notices of Enforcement Discretion.

Get The FREE
HIPAA Compliance Checklist
Immediate Delivery of Checklist Link To Your Email Address
Please enter correct email address
Your Privacy Respected
HIPAA Journal Privacy Policy
This article explains HIPAA requirements in more detail and can be used in conjunction with our HIPAA checklist to understand what is required to ensure compliance.
Summary Of Article Contents
Why Use The HIPAA Compliance Checklist?
Being aware of your compliance obligations and those of your business partners can be vital because, in the event of a HIPAA violation, ignorance of the HIPAA requirements is not an acceptable defense against enforcement action.
Although the majority of enforcement actions do not result in civil monetary penalties, complying with a corrective action plan (the most common violation resolution) will incur indirect costs and disrupt business activities.
HIPAA Compliance For Organizations
The first issue to address is whether or not your organization is subject to the Administrative Simplification provisions of the Healthcare Insurance Portability and Accountability Act (HIPAA); and, if so, which provisions apply.
Who Is HIPPA Applicable To?
Generally, organizations subject to all the Administrative Simplification provisions are health plans, health care clearing houses, and healthcare providers that transmit health information in electronic form in connection with a transaction for which a HIPAA standard exists.
Covered Entities
Organizations that meet these criteria are referred to in HIPAA as Covered Entities. However, it is important to note there are multiple exceptions to the criteria. For example, health plans that provide “excluded benefits” are not Covered Entities, on-campus health centers that only provide medical services for students are not Covered Entities, and paper-to-paper non-digital fax communications are not considered electronic transmissions.
Business Associates
Business partners (referred to as Business Associates in HIPAA) are generally subject to some – but not all – of the Administrative Simplification provisions depending on the type of service they perform for, or on behalf of, a Covered Entity. Generally, Business Associates are required to comply with the Security Rule and Breach Notification provisions, §164.500(c) of the Privacy Rule, and any parts of the Administrative Requirements or Privacy Rule provisions stipulated in a Business Associate Agreement.
Not every business partner is a Business Associate. A business partner is only a Business Associate if it creates, receives, maintains, or transmits Protected Health Information (PHI) for a function or activity regulated by HIPAA. Business partners providing services for, or on behalf, of Covered Entities that do not involve a use or disclosure of PHI are not subject to the Administrative Simplification provisions of HIPAA.
Exceptions
Other exceptions exist with regards to members of a Covered Entity´s or Business Associate´s workforce. Workforce members under “the direct control” of a Covered Entity or Business Associate – whether paid or not – are not Business Associates but are required to comply with provisions relevant to their roles via policies and procedures implemented by the Covered Entity or Business Associate for whom they work.
Finally, if a health plan or healthcare provider does not qualify as a Covered Entity (because of an exception) but provides a service to or on behalf of an organization that does qualify as a Covered Entity, the exempted organization must comply with the Security Rule provisions and Breach Notification provisions, and any parts of the Privacy Rule provisions stipulated in a Business Associate Agreement.

Get The FREE
HIPAA Compliance Checklist
Immediate Delivery of Checklist Link To Your Email Address
Please enter correct email address
Your Privacy Respected
HIPAA Journal Privacy Policy
HIPAA Compliance Checklist to Determine If Your Organization Is Subject to HIPAA as a Covered Entity or a Business Associate
This additional set of HIPAA compliance checklists will help you determine whether or not your organization is subject to the Administrative Simplification provisions of HIPAA; and, if so, which provisions apply.
Is your organization:
|
□ |
Is your organization:
|
□ |
Are you, or is your organization:
|
□ |
If you have ticked any of the boxes in the above HIPAA compliance checklist for organizations, your organization is a Covered Entity and required to comply with the applicable Administrative Simplification provisions of the Privacy, Security, and Breach Notification Rules.
Do you, or does your organization:
|
□ |
Is your organization:
|
□ |
Do you, or does your organization:
|
□ |
If you have ticked any of the boxes in the above HIPAA compliance checklist – and you have not already qualified as a Covered Entity – you or your organization are a Business Associate.
As such, your organization must respect HIPAA requirements to comply with the applicable Administrative Simplification provisions of the Security and Breach Notification Rules and any Administrative Requirements or Privacy Rule provisions stipulated in a Business Associate Agreement.
Not A Covered Entity Or Business Associate?
If you have ticked none of the boxes in the above HIPAA compliance checklists, this does not necessarily mean you are not required to comply with some Administrative Simplification provisions of HIPAA. For example, vendors of personal health records (“PHRs”) and PHR-related entities are required to comply with the HIPAA Breach Notification Rule even though neither a Covered Entity nor a Business Associate.

Get The FREE
HIPAA Compliance Checklist
Immediate Delivery of Checklist Link To Your Email Address
Please enter correct email address
Your Privacy Respected
HIPAA Journal Privacy Policy
 HIPAA Privacy Rule
HIPAA Privacy Rule
The HIPAA Privacy Rule establishes national standards to protect individuals’ medical records and other individually identifiable health information (defined as PHI when maintained or transmitted by a Covered Entity) in whatever format it is created, received, maintained, or transmitted (e.g., oral, written, or electronic).
The Rule requires appropriate safeguards to protect the privacy of PHI and sets limits on the uses and disclosures that may be made of such information without an individual’s authorization.
The Privacy Rule also gives individuals rights over their PHI – including the right to obtain a copy of PHI maintained in a designated record set, request corrections if errors exist, and transfer some or all the PHI maintained in the record set to another provider.
Individuals also have the right to request an accounting of disclosures – a record of uses or disclosures of PHI over the previous six years except certain permissible or authorized disclosures.
Although the Privacy Rule applies to fewer organizations than the Security Rule, it is best to start on the path to compliance with a HIPAA checklist that relates to privacy and individuals´ rights. This is because the Privacy Rule is the foundation for every other HIPAA Rule; and, even if your organization is not required to comply with the Privacy Rule provisions, an understanding of what they are and their purpose is virtually essential for compliance with HIPAA´s other Rules.
The following HIPAA Privacy Rule checklist should be regarded as a starting point for any subsequent HIPAA compliance checklist that may be more appropriate for your organization.
- Designate a HIPAA Privacy Officer responsible for the development, implementation, and enforcement of HIPAA-compliant policies.
- Understand what PHI is, how it can be used and disclosed in compliance with HIPAA, and when an individual´s authorization is required.
- Identify risks to the privacy of PHI and implement safeguards to minimize risks to a “reasonable and appropriate” level.
- Develop policies and procedures for using and disclosing PHI in compliance with HIPAA and for preventing HIPAA violations.
- Develop policies and procedures for obtaining authorizations and for giving individuals an opportunity to agree or object when required.
- Develop and distribute a Notice of Privacy Practices explaining how the organization uses and discloses PHI and outlining individuals´ rights.
- Develop policies and procedures for managing patient access requests (to their PHI), correction requests, and data transfer requests.
- Develop procedures for members of the workforce to report HIPAA violations and for the organization to fulfil its breach notification requirements.
- Train members of the workforce on the policies and procedures relevant to their roles and on general HIPAA compliance.
- Develop and distribute a sanctions policy outlining the sanctions for non-compliance with the organization´s HIPAA policies.
- Perform due diligence on Business Associates, review existing Business Associate Agreements, and revise as necessary.
- Develop and document a contingency plan for responding to an emergency that damages systems or physical locations in which PHI is maintained.
What Should a HIPAA Risk Assessment Checklist Consist Of?
Before moving ahead with other types of HIPAA compliance checklists, it is worth discussing what a HIPAA risk assessment checklist should consist of. This is because there is a lack of guidance as to what risks should be assessed and how risk assessments should be analyzed.
The Department of Health and Human Services (HHS) has explained that the failure to provide a “specific risk analysis methodology” is due to Covered Entities and Business Associates being of different sizes, capabilities, and complexity.
However, HHS does provide guidance on the objectives of a HIPAA risk assessment checklist:
- Identify the PHI that your organization creates, receives, stores, and transmits – including PHI shared with consultants, vendors, and Business Associates.
- Identify the human, natural, and environmental threats to the integrity of PHI – human threats including those which are both intentional and unintentional.
- Assess what measures are in place to protect against threats to the integrity of PHI, and the likelihood of a “reasonably anticipated” breach occurring.
- Determine the potential impact of a PHI breach and assign each potential occurrence a risk level based on the average of the assigned likelihood and impact levels.
- Document the findings and implement measures, procedures, and policies where necessary to tick the boxes on the HIPAA compliance checklist and ensure HIPAA compliance.
- The HIPAA risk assessment, the rationale for the measures, procedures, and policies subsequently implemented, and all policy documents must be retained for a minimum of six years.
As mentioned above, a HIPAA risk assessment checklist is not a one-time requirement, but a regular task necessary to ensure continued HIPAA compliance.
The HIPAA risk assessment and an analysis of its findings will help organizations to comply with many other areas on our HIPAA compliance checklist and should be reviewed whenever changes to the workforce, work practices, or technology occur.
Depending on the size, capability, and complexity of an organization, compiling a fully comprehensive HIPAA risk assessment can be an extremely long-winded task.
There are various online tools that can help organizations with the compilation of a HIPAA risk assessment; although, due to the lack of a “specific risk analysis methodology”, there is no one-size-fits-all solution.

Get The FREE
HIPAA Compliance Checklist
Immediate Delivery of Checklist Link To Your Email Address
Please enter correct email address
Your Privacy Respected
HIPAA Journal Privacy Policy
HIPAA Security Rule Checklist
 The HIPAA Security Rule checklist contains standards designed to ensure the confidentiality, integrity, and availability of PHI created, received, maintained, or transmitted electronically (ePHI). The HIPAA Security Rule consists of five sections – each of which is described in detail below, along with a HIPAA Security Rule Checklist that summarizes the key HIPAA Security Rule requirements.
The HIPAA Security Rule checklist contains standards designed to ensure the confidentiality, integrity, and availability of PHI created, received, maintained, or transmitted electronically (ePHI). The HIPAA Security Rule consists of five sections – each of which is described in detail below, along with a HIPAA Security Rule Checklist that summarizes the key HIPAA Security Rule requirements.
The General Rules
This first section of the HIPAA Security Rule is frequently overlooked, yet it contains a number of key instructions to Covered Entities and Business Associates about their compliance obligations. For example, the General Rules stipulate that Covered Entities and Business Associates must:
- Protect against any reasonably anticipated threats or hazards to the security or integrity of ePHI.
- Protect against any reasonably anticipated uses or disclosures of PHI that are not permitted by the Privacy Rule.
- Ensure compliance with the Security Rule by workforce members.
These are not lightweight instructions and imply organizations must identify reasonably anticipated threats and hazards, and potential impermissible uses and disclosures, implement measures to protect against them, and then monitor user activity to ensure workforces comply with Security Rule policies and procedures implemented by the organization.
The Security Rule safeguards (in sections two, three, and four) provide the minimum measures that must implement to comply with these instructions, but it is important to be aware that if a reasonably anticipated threat or hazard exists that is not covered by these minimum measures, organizations are responsible for developing and implementing additional measures.
In this respect, the General Rules allow for a “flexibility of approach”. The flexibility of approach clause gives organizations leeway to determine what security measures are suitable to mitigate threats, hazards, and the risk of impermissible uses and disclosures depending on their size, existing security capabilities, and the criticality of identified risks.
However, the flexibility of approach does not excuse Covered Entities and Business Associates from complying with all the Security Rule safeguards unless an implementation specification is “addressable” and either the safeguard is not reasonable or appropriate or an equivalent alternative measure would be equally – or more – effective.
The Administrative Safeguards
The Administrative Safeguards are the backbone of Security Rule compliance as they require that a Security Officer is designated with responsibility for conducting risk analyses, implementing measures to reduce risks and vulnerabilities, workforce training, oversight of IT continuity, and Business Associate Agreements.
There is some crossover between the Security Officer and Privacy Officer roles as both are required to develop a contingency plan to ensure business continuity and perform due diligence on Business Associates.
This is likely because some Business Associates will not be subject to the Privacy Rule yet have to have to ensure business continuity and have Business Associate Agreements in place with subcontractors.
| Standard | Further Information |
| Security Management Process | Organizations must conduct risk analyses, implement measures to reduce risks and vulnerabilities, implement a workforce sanctions policy, and implement procedures to review system activity. |
| Assign Security Responsibility | Designate a HIPAA Security Officer responsible for the development, implementation, and enforcement of Security Rule procedures and policies. This can be the same person as the HIPAA Privacy Officer. |
| Workforce Security | Members of the workforce should have clearance before accessing systems containing ePHI and measures must be implemented to limit access to ePHI and terminate access when they change roles or end their employment. |
| Information Access Management | This standard applies to hybrid and affiliated organizations to ensure ePHI is only accessed by members of “covered” organizations´ workforces and not by workforce members of parent, joint, or affiliated organizations. |
| Security Awareness and Training | Members of the workforce – even those with no access to ePHI – must participate in an ongoing security awareness training program. This standard also includes security reminders and password management. |
| Security Incident Procedures | The standard requires Covered Entities and Business Associates to adopt measures for reporting, responding to, and documenting the outcomes of security incidents (Note: Not limited to cybersecurity incidents). |
| Contingency Plan | Establish (and test) policies and procedures to respond to an emergency. The policies and procedures must include a data backup plan, a disaster recovery plan, and an emergency mode operating plan. |
| Periodic Evaluations | This standard requires Covered Entities and Business Associates to periodically review the policies, procedures, and measure implemented to comply with the Security Rule – including Business Associate Agreements. |
The Physical Safeguards
The Physical Safeguards focus on physical access to ePHI irrespective of its location.
ePHI could be stored in a remote data center, in the cloud, or on servers which are located within the organization´s premises.
The Physical Safeguards also stipulate how workstations and mobile devices should be secured against unauthorized access.
| Standard | Further Information |
| Facility Access Controls | Although this standard applies to physical access to electronic information systems and the facilities in which they are housed, measures should also be put in place to limit physical access to paper PHI whenever possible. |
| Workstation Use | There are various interpretations of this standard – the most secure interpretation being prohibiting non-business activity on workstations and devices used to create, receive, maintain, or transmit ePHI. |
| Workstation Security | This standard requires Covered Entities and Business Associates to implement safeguards so that physical access to workstations and devices is limited to only members of the workforce with appropriate authorization. |
| Device and Media Controls | The implementation specifications attached to this standard include the disposal or re-use of media on which ePHI has been stored and maintaining an inventory of devices and media used by the organization to access ePHI. |
The HIPAA Technical Safeguards
The HIPAA Technical Safeguards are designed to make sure each person accessing ePHI is who they say they are, that they do what they are supposed to do; and that, if an issue manifests due to an accidental or malicious action, the issue is identified and rectified at the earliest possible opportunity.
| Access Controls | This standard not only relates to user identification and password management, but also includes implementation specifications relating to automatic logoff, encryption, and emergency access procedures |
| Audit Controls | The audit controls standard requires Covered Entities and Business Associates to implement software that records event logs and examines activity on systems containing ePHI. |
| Integrity Controls | As an addition to the above standard, controls have to be implemented to ensure ePHI is not altered or destroyed improperly. This is as much to mitigate the threat of malicious insiders as external threats. |
| Person or Entity Authentication | This standard is practically identical to the user identification requirements of the Access Controls standard and demonstrates the importance of implementing and enforcing an effective password management policy. |
| Transmission Security | Unlike the Integrity Controls standard that applies to ePHI when accessed by an authorized user, this standard requires measures are put in place to ensure the integrity of ePHI in transit and prevent unauthorized destruction. |
 Organizational Requirements
Organizational Requirements
There are several sections of the Administrative Simplification provisions entitled Organizational Requirements, but whereas the others relate to “non-general scenarios” (e.g., hybrid entities and health plan uses and disclosures), the Organizational Requirements of the Security Rule are relevant to most Covered Entities and Business Associates as they cover Business Associate Agreements.
Business Associate Agreements are also covered elsewhere in the Administrative Simplification provisions, but it is important for organizations in a business relationship in which ePHI is disclosed to be aware of this specific section because it stipulates:
- Business Associate Agreements must provide that the Business Associate complies with the applicable parts of the Security Rule,
- Business Associates that subcontract services in which ePHI is disclosed must enter into an Agreement with the subcontractor, and
- Business Associates will report any security incident – including, but not limited to, breaches of unsecured ePHI – to the Covered Entity the Agreement is with.
There are additional requirements in the Organizational Requirements for when a health plan discloses ePHI to a plan sponsor, and these are very similar to the Organizational Requirements relating to hybrid entities.
The Security Rule then concludes with standards relating to document retention which are discussed in further depth in the section explaining the HIPAA Audit Checklist.
HIPAA Security Requirements
Although no standard in the Security Rule is any more important than any other, some are key to a HIPAA Security Rule checklist because – without them – it would be difficult to comply with the Rule in its entirety. The list compiled below are the twelve essential components of a HIPAA security requirements checklist.
- Designate a HIPAA Security Officer. The role can be assigned to the HIPAA Privacy Officer; but in larger organizations, it is best to designate the role to a member of the IT team.
- Determine which systems create, receive, maintain, or transmit ePHI and protect them from unauthorized access from other parts of the organization´s IT infrastructure.
- Implement measures that mitigate the threats from malware, ransomware, and phishing. For example, advanced email and Internet filters with malicious URL detection capabilities.
- Establish which workforce members should have access to ePHI and implement Role-Based Access Controls to prevent users accessing more ePHI than they are supposed to.
- Implement a system for verifying the identity of workforce members to comply with the physical access, workstation security, and event logging requirements of the Security Rule.
- Conduct an inventory of devices used to access ePHI and the media on which it is stored. Ensure a system is in place to record any movement of devices and media.
- Ensure all devices used to access ePHI – including remote and personal devices – are PIN-locked and have automatic logoff capabilities activated to prevent unauthorized access.
- Put processes in place for authorized workforce members to report security incidents or escalate security concerns to the Security Officer or Security Operations Center.
- Implement a security awareness training program for all members of the workforce that incorporates how to escalate security concerns and incident reporting procedures.
- Develop a sanctions policy explaining the sanctions for violating the organization´s security policies and distribute it among all members of the workforce (even those with no access to ePHI).
- Develop a contingency plan for foreseeable events that may threaten the confidentiality, integrity, and availability of ePHI, and test the plan against each type of event.
- Review existing Business Associate Agreements relating to disclosures of ePHI and replace any that fail to comply with the Organizational Requirements of the HIPAA Security Rule.

Get The FREE
HIPAA Compliance Checklist
Immediate Delivery of Checklist Link To Your Email Address
Please enter correct email address
Your Privacy Respected
HIPAA Journal Privacy Policy
The HIPAA Breach Notification Rule
 All organizations that create, receive, maintain, or transmit PHI or ePHI have to comply with the HIPAA Breach Notification Rule. This includes organizations not covered by the Privacy and Security Rules such as vendors of personal health records (“PHRs”), PHR-related entities (i.e., fitness tracker services that send data to or access data on a PHR), and third-party service providers.
All organizations that create, receive, maintain, or transmit PHI or ePHI have to comply with the HIPAA Breach Notification Rule. This includes organizations not covered by the Privacy and Security Rules such as vendors of personal health records (“PHRs”), PHR-related entities (i.e., fitness tracker services that send data to or access data on a PHR), and third-party service providers.
All organizations required to comply with the Breach Notification Rule must be prepared to notify individuals, the relevant federal agency, and – in some cases – local media when a breach of unsecured PHI/ePHI occurs. In such events, it is important to fulfil all the applicable requirements of the Breach Notification Rule, even if the breach relates to the health record of a single individual.
However, before actioning breach notification procedures, it is important for organizations to establish whether the breach is reportable or not. Unnecessarily reporting a data breach will likely result in an unnecessary investigation which, even if no violation is found, will result in some level of business disruption in addition to unnecessary concerns for the individual(s) affected.
In the event of a suspected data breach, organizations should make sure that any breach is reportable by first conducting a risk assessment or taking advantage of a HIPAA breach decision tool/HIPAA breach risk assessment form to determine:
- Was ePHI encrypted and unreadable, undecipherable, and unusable?
- If not, what health information and identifiers were exposed in the breach?
- Who (if known) acquired, accessed, or viewed PHI/ePHI impermissibly?
- What is the likelihood of the data being further used or disclosed?
- What measures are in place to mitigate the effect of the breach?
If a breach is reportable, individuals must be notified on the breach within sixty days. The breach notification must include information about what data has been disclosed, what the organization is doing to mitigate the effects of the breach and prevent further security incidents, and what the individual can do to best protect themselves from theft or fraud.
If the breach affects fewer than 500 individuals, organizations have until the end of each calendar year to notify HHS´ Office for Civil Rights or Federal Trade Commission. Breaches affecting 500 or more individuals must be notified to the appropriate agency and the local media within sixty days – the failure to do so attracting stiffer HIPAA violation penalties from HHS´ Office for Civil Rights or a fine of up to $46,517 per day from the Federal Trade Commission.
What is HIPAA Compliance?
HIPAA compliance is complying with the applicable standards, requirements, and implementation specifications of the HIPAA Administrative Simplification Regulations (45 CFR Parts 160,162, and 164) – unless an exception exists in §160.203, or unless an alternative state or federal law has more stringent privacy requirements than HIPAA or provides individuals with more rights.
Covered Entities and Business Associates are required (by §164.306) to protect against any reasonably anticipated uses and disclosures of PHI not permitted by the Privacy Rule, and any reasonably anticipated threats to the security of PHI not covered by the Security Rule – even if no specific standard exists relating to the impermissible use or disclosure or threat to security.
In some cases, this means HIPAA compliance can go beyond the standards, requirements, and implementation specifications published by the Department for Health and Human Services depending on the nature of an organization’s activities, its operational structure, and any unique circumstances that could result in the necessity for additional policies, procedures, or safeguards.
Applicability and the Flexibility of Approach
Two important considerations in calculating an organization’s HIPAA compliance obligations are applicability and the flexibility of approach. Applicability is important because different standards apply to different organizations depending on whether they are a health plan, a health care clearinghouse, a healthcare provider (that qualifies as a Covered Entity), or a Business Associate.
Not every organization that qualifies as a Covered Entity or Business Associate has to comply with every standard, requirement, or implementation specification – only those that apply to the nature of its operations. In some cases, the Administrative Simplification Regulations distinguish between which standards apply to which type of organization, but that is not always the case.
With regards to the flexibility of approach, this was briefly discussed above. In the context of answering the question what is HIPAA compliance it is worth revisiting this clause to more fully explain what it means. According to §164.306, when a Covered Entity of Business Associate decides which security measures to implement, the choice can be influenced by:
- The size, complexity, and (human) capabilities of the organization.
- The existing IT structure, hardware, and software security capabilities.
- The cost of implementing the standard or implementation specification.
- The probability and criticality of potential risks and threats to PHI.
As mentioned above, the flexibility of approach clause does not excuse Covered Entities and Business Associate from elements of HIPAA compliance. However, determining which standards are applicable to an organization – and where flexibility of approach applies – can complicate HIPAA compliance and make it harder to identify an organization’s compliance obligations without leaving compliance gaps.
5 Tips for a HIPAA Compliance Program
In 2011, HHS’ Office of the Inspector General published a series of tips for a healthcare compliance program. There have been multiple changes to healthcare compliance since 2011, and the following tips for a HIPAA compliance program reflect these changes. Before starting a HIPAA compliance program, it is first important to identify which HIPAA standards are applicable to your organization.
Thereafter, each organization should designate the role of a HIPAA Privacy Officer (even if one is not mandated because the organization qualifies as a Business Associate) and a HIPAA Security Officer. Wherever possible, the Officers should be supported by a compliance team drawn from departments such as legal, administration, security, IT, and – without doubt – medical.
Tip #1 – Develop policies and procedures to comply with the applicable standards of the Privacy, Security, and Breach Notification Rules.
Tip #2 – Implement necessary administrative, physical, and technical safeguards taking into account risk analyses and the allowed flexibility of approach.
Tip #3 – Develop an effective HIPAA training program taking into account any reasonably anticipated threats to the privacy and security of PHI.
Tip #4 – Monitor compliance and ensure channels of communication exist to seek advice and report concerns, violations, and breaches.
Tip #5 – Respond to requests for advice and reports of violations promptly and enforce a sanctions policy fairly and equally.
While HHS’ original tips from 2011 might now be out-of-date, some of the publication’s closing comments are just as valid in 2023 as they were then. Make compliance plans a priority now (and you can use our HIPAA compliance checklists to do that), identify your fraud and abuse risk areas, and when in doubt ask for help – ideally from a HIPAA compliance professional.
HIPAA IT Compliance
HIPAA IT compliance is sometimes confused with simply implementing the Safeguards of the Security Rule, but often much more is required for IT departments to be HIPAA IT compliant. For example, as most PHI is now maintained on electronic systems, IT departments have to consider how best to respond to individuals exercising their rights to access, correct, and transfer PHI.
In this scenario, IT departments may be responsible for determining what data is maintained in a designated record set, what happens to data excluded from the designated record set, how information collected orally or on paper is added to the designated record set, and how the process for accounting of disclosures is managed – all Privacy Rule issues.
Due to likely being involved in the transfer of ePHI to or from Business Associates, IT departments may need to be involved in the due diligence process and will likely be the first port of call in the event of a Business Associate security incident, so may need to know which party will be responsible for complying with the breach notification requirements.
It is also possible that representatives from the IT department will be involved in selected health care operations in which PHI is used or disclosed permissibly (i.e., provider or health plan evaluations, fraud and abuse detection, business planning, etc.). In such cases, they will also need to be aware of the Minimum Necessary Standards and rules concerning incidental disclosures.
Additional HIPAA IT Requirements
In addition to the above – and implementing the Safeguards of the Security Rule – additional HIPAA IT requirements may include updating existing security mechanisms to meet the requirements of a “recognized cybersecurity framework” (see “Updates to HIPAA Compliance” below), preparing legacy systems for migration to the cloud, and monitoring user activity.
Ultimately – once a recognized security framework in in place and legacy systems are migrated to the cloud – it may be possible to automate many monitoring tasks. However, due to the evolving nature of cyberthreats, it will not be possible to automate periodic risk assessments and analyses and may not be possible to adjust quickly to new forms of malware, ransomware, and phishing.
Cyberattacks are not the only things that are evolving. The healthcare and health insurance landscapes are also evolving with new rules and guidance frequently being issued by HHS´ Office for Civil Rights, CMS, and the FTC. Furthermore, it is not just federal laws that IT departments have to comply with, but state laws as well.
Consequently, many IT departments have compliance requirements additional to HIPAA. Most states have privacy laws with at least one element preempting HIPAA, while some state laws extend beyond borders to protect citizens wherever they are (i.e., Texas). Organizations that treat international patients may also have to comply with the EU´s General Data Protection Regulation.
HIPAA IT Compliance Checklist
Bearing in mind the Security Rule´s “flexibility of approach”, that some smaller organizations will have limited resources, and that some larger organizations will have unique compliance challenges, there is no one-size-fits-all HIPAA IT compliance checklist. With this in mind, the following list of best practices are guidelines that can help IT departments meet the HIPAA IT requirements.
- Understand which international, federal, and state laws your organization has to comply with and develop policies and procedures accordingly.
- Enforce a password policy that requires the use of unique, complex passwords for each account and support the policy with mandatory MFA where practical.
- Automate monitoring and reporting as much as possible to reduce the administrative burden of user compliance and threat management.
- Test incident response and disaster recovery plans for every conceivable event. Ensure all team members understand their roles during such events.
- Separate the infrastructure into a data layer and system layer to support the integrity of the system and isolate attacks on the system.
- Implement encoding or blockchain technologies to prevent tampering and support compliance efforts to ensure the integrity of ePHI.
- Prepare for the possibility that account credentials may be compromised and have processes ready to shut down compromised accounts remotely.
- Map data flows – including those to/from Business Associates – to simplify risk assessments and analyses and more efficiently identify threats to ePHI.
- Don´t assume all users have the same level of knowledge, awareness, or susceptibility. Identify where user weaknesses exist to build stronger defenses against cyberattacks.
- Connect with third party compliance experts if you need assistance completing a HIPAA IT compliance checklist. You cannot leave security to chance!
HIPAA Audit
 The final HIPAA compliance checklist concerns HIPAA audits. While OCR´s audit program may not be as active as it was a few years ago, it is still beneficial to prepare for a compliance audit as the documentation requested in an audit is the same as requested in an investigation conducted by a federal agency in response to a data breach or complaint. As with the HIPAA IT compliance checklist, there is no one-size-fits-all HIPAA audit checklist.
The final HIPAA compliance checklist concerns HIPAA audits. While OCR´s audit program may not be as active as it was a few years ago, it is still beneficial to prepare for a compliance audit as the documentation requested in an audit is the same as requested in an investigation conducted by a federal agency in response to a data breach or complaint. As with the HIPAA IT compliance checklist, there is no one-size-fits-all HIPAA audit checklist.
In order to help HIPAA Covered Entities and Business Associates compile a checklist in preparation for the OCR audit program, the Department of Health and Human Services published audit protocols for the first two rounds of audits. You can find a link to OCR´s audit protocols in our dedicated HIPAA Audit Checklist page, along with suggestions for compiling internal HIPAA audit checklists.
How to Become HIPAA Compliant
It has been mentioned several times during this article that there is no one-size-fits-all HIPAA compliance checklist. However, although not all the Rules apply to all organizations, the basics of HIPAA compliance are the same for every type of Covered Entity, Business Associate, and PHR-related entity – protect the privacy of individually identifiable health information and ensure the confidentiality, integrity, and availability of ePHI.
Ultimately, it will likely be necessary for each Privacy Officer and each Security Officer to develop their own HIPAA compliance checklist in order to address unique challenges. We hope that this article has provided some pointers to what should be included on each type of checklist; but, if doubts exist about the comprehensiveness of an organization´s compliance efforts, it is in the organization´s best interest to speak with a professional HIPAA compliance advisor.

Get The FREE
HIPAA Compliance Checklist
Immediate Delivery of Checklist Link To Your Email Address
Please enter correct email address
Your Privacy Respected
HIPAA Journal Privacy Policy
HIPAA Compliance Checklist: FAQs
Who is this HIPAA Compliance Checklist For?
This HIPAA compliance checklist is for HIPAA Privacy Officers, HIPAA Security Officers, and any other member of a Covered Entity’s or Business Associate’s workforce assigned the task of HIPAA compliance. The checklist can also be shared between departments if different departments are responsible for complying with specific areas of HIPAA.
What is a HIPAA Compliance Checklist?
A HIPAA compliance checklist consists of the basic compliance requirement of the HIPAA Privacy, Security, and Breach Notification Rules. Some areas of the checklist may not apply to some organizations depending on the nature of their activities, while some organizations will have to consider additional checklist items if they are involved in certain activities (i.e., psychiatrists).
Is there a specific HIPAA Compliance Checklist for IT?
There is no specific HIPAA compliance checklist for IT because the scale of IT operations can vary between different organizations depending on their size, complexity, and processes. If a HIPAA compliance checklist for IT is thought necessary, organizations are advised to conduct an IT compliance audit to see what items may be necessary to include.
What Does HIPAA Compliance Mean?
HIPAA compliance means complying with the standards and implementation specifications of the HIPAA Privacy, Security, and Breach Notification Rules. However, it is necessary to be aware that the General Rules of the Security Rule (§164.306) allow for a “flexibility of approach” Covered Entities and Business Associates should bear this clause in mind when reviewing HIPAA requirements.
Who is Responsible for Implementing and Monitoring the HIPAA Regulations?
The agency responsible for implementing and monitoring the HIPAA regulations is the Department of Health and Human Services (HHS). Within HHS, two departments are responsible for enforcing the HIPAA regulations – the agency´s Office for Civil Rights (OCR) is responsible for taking enforcement action for violations of the Privacy, Security, and Breach Notification Rule, while the Centers for Medicare and Medicaid Services (CMS) enforce the Administrative Requirements of HIPAA.
What is the Key to HIPAA Compliance?
The key to HIPAA compliance is remembering that compliance is an ongoing process and not a one-off exercise. It is important to have mechanisms in place to prevent shortcuts becoming the norm and developing into a culture of non-compliance – which then becomes harder to reverse and may lead to more noncompliant shortcuts being taken “to get the job done”.
Who Must Comply with the HIPAA Security Rule?
Compliance with the HIPAA Security Rule is required for all individuals and organizations that qualify as Covered Entities. Business Associates and subcontractors with whom PHI is shared must also comply with the Security Rule, as must healthcare organizations and insurance companies that do not qualify as Covered Entities but provide a service for or on behalf of another Covered Entity as a Business Associate.
What does the HIPAA Security Rule Apply To?
The Security Rule applies to all Protected Health Information that is created, collected, maintained, or transmitted electronically (ePHI). It is important to be aware that ePHI is a subset of PHI, and some Privacy Rule standards may also apply – especially those relating to permissible uses and disclosures and the Minimum Necessary Standard.
What is the Health Insurance Portability and Accountability Act (HIPAA)?
The Health Insurance Portability and Accountability Act is an Act passed in 1996 with the intention of reforming the health insurance industry. It facilitated the portability of health insurance from one employer to another to avoid workers being locked in an unsuitable job for fear of losing health coverage and stopped health plans discriminating against workers with pre-existing conditions.
To prevent the costs of increased portability and accountability being passed on to employers and plan members in the form of higher premiums, Title II of HIPAA introduced measures to reduce fraud against the health insurance industry and make the processing of health insurance claims more efficient. These measures led to the Administrative Simplification regulation which includes the Privacy, Security, and Breach Notification Rules.
What are the HIPAA Compliance Requirements?
Although HIPAA compliance requirements are mentioned periodically in the above HIPAA compliance checklist, there is no one-size-fits-all set of requirements. Each Covered Entity and Business Associate must determine its own HIPAA compliance requirements based on a risk assessment and what “reasonable and appropriate” measures are required to be compliant.
What are the Guidelines to Stay HIPAA Compliant?
The guidelines to stay HIPAA compliant can be interpreted in several ways. For example, it can mean the standards of the Privacy, Security, and Breach Notification Rules, the safeguards of the Security Rule, or the policies developed by an organization´s HIPAA Privacy and Security Officers to ensure the organization and members of the organization’s workforce stay HIPAA compliant.
What Do You Need to Know about HIPAA?
The most important thing you need to know about HIPAA is that ignorance of the HIPAA requirements is no defense against enforcement action. If you are a HIPAA Covered Entity or a Business Associate with access to Protected Health Information, you need to understand what the rules are, how they apply to you, and what you need to do to become HIPAA compliant.
What are the Penalties for Breaching HIPAA?
The penalties for breaching HIPAA vary according to the nature of the violation, the level of culpability, and the amount of assistance given to HHS during investigations into the breach. The current penalty structure was implemented in the HITECH Act 2009 and penalty amounts increase each year to account for inflation. The most recent penalties for breaching HIPAA can be found here.
What Steps Should You Take for HIPAA Compliance?
The steps you should take for HIPAA compliance depend on the nature of your business and your access to Protected Health Information. The HHS publishes several tools to help Covered Entities determine what steps to take for HIPAA compliance; but, if you are still unsure about HIPAA requirements, you should seek professional compliance advice.
What is the HIPAA Security Rule?
The HIPAA Security Rule was enacted in 2004 to establish national standards for the protection of Protected Health Information when it is created, received, used, or maintained electronically by a Covered Entity. The Rule was introduced due to more Covered Entities adopting technology and replacing paper processes.
What is the HIPAA Privacy Rule?
The HIPAA Privacy Rule – or the “Standards for Privacy of Individually Identifiable Health Information” – was introduced to standardize a patchwork of state laws relating to how healthcare providers and insurers can use, share, and disclose Protected Health Information. It is important to note that where state laws provide stronger privacy protections, these laws continue to apply.
What is the HIPAA Breach Notification Rule?
The HIPAA Breach Notification Rule requires Covered Entities and Business Associations to notify the Secretary of Health and Human Services of any impermissible use or disclosure of unsecured Protected Health Information. Different procedures apply depending on the nature of the breach and the number of records disclosed.
What is the HIPAA Omnibus Rule?
The HIPAA Omnibus Rule was enacted in 2013 to update elements of the Privacy, Security, Enforcement, and Breach Notification Rules, and activate elements of the HITECH Act. Significantly for Covered Entities and Business Associates, it gave the Department of Health and Human Services more resources to investigate breaches and impose fines for non-compliance.
What is the HIPAA Enforcement Rule?
The HIPAA Enforcement Rule explains the procedures under which the Department of Health and Human Services will conduct investigations, manage hearings, and impose penalties for HIPAA violation cases. It is important to note other agencies (for example Centers for Medicare and Medicaid Services) can take HIPAA enforcement actions, and these may have their own procedures.
What is the Minimum Necessary Rule?
The Minimum Necessary Rule – sometimes called the “Minimum Necessary Standard” or “Minimum Necessary Requirement” – is a key element of the HIPAA Privacy Rule. The Rule stipulates that HIPAA-covered entities make reasonable efforts to ensure access to PHI is limited to the minimum necessary to accomplish the intended purpose of a particular use, disclosure, or request – and nothing more.
What are the HIPAA Retention Requirements?
The HIPAA retention requirements relate to how long Covered Entities must retain HIPAA-related procedures, policies, and other documentation. In states that do not require longer retention periods, the minimum length of time for HIPAA-related documentation to be retained is six years. You will find examples of what types of documentation should be retained in this article.
Are there Rules about Sharing PHI on Social Media?
There are no specific Rules about sharing PHI on social media because the HIPAA Privacy Rule was enacted many years before most social media platforms existed. However, except for permitted uses, the disclosure of personal identifiable information without a patient´s consent is a violation of HIPAA, and sharing PHI on social media would come into this category.
What is the Difference between Patient Consent and Patient Authorization in HIPAA?
The difference between patient consent and patient authorization in HIPAA is that patient consent can be verbal, whereas patient authorization has to be written. There are very few scenarios in which patient consent is allowed by HIPAA; and, for most uses and disclosures of PHI not expressly permitted by the Privacy Rule a Covered Entity has to obtain a patient’s written authorization via a HIPAA Release Form.
Are Pagers HIPAA-Compliant Communication Tools?
Pagers can be HIPAA-compliant communication tools depending on what they are being used for and what capabilities they have. If a pager is not being used to communicate ePHI, HIPAA compliance is not an issue. If a pager is being used to communicate ePHI, it has to have capabilities such as user authentication, remote wipe, and automatic log-off. You can find out more about pagers and HIPAA compliance in this article.
How Does the EU´s General Data Protection Regulation Affect HIPAA Compliance?
While the EU´s General Data Protection Regulation doesn´t affect HIPAA compliance in any way, it does introduce a further set of regulations for Covered Entities and Business Associates that collect, process, share, or store data relating to EU citizens – for example if an EU citizen receives medical treatment in the USA. This article provides more information about GDPR for US companies.
What are the Administrative Simplification Provisions of HIPAA?
The Administrative Simplification provisions of HIPAA consist of the General Administrative Requirements (Part 160), the Transaction, Code Sets, and Identifier Standards (Part 162) and the Privacy, Security, and Breach Notification Rules (Part 164). The Department of Health and Human Services has combined the provisions into a single PDF for ease of reference.
Why Might My Organization Need to Know a Business Partner´s Compliance Obligations?
Your organization might need to know a business partner’s compliance obligations if it intends to share PHI with a Business Associate. Before a Covered Entity discloses PHI to a Business Associate, it is important to conduct due diligence on the Business Associate to ensure the privacy of the PHI is protected and safeguards are in place to ensure the confidentiality, integrity, and availability of ePHI. It is not enough to rely on the undertakings of a Business Associate Agreement.
What are the Excluded Benefits that would Exempt a Health Plan from being a Covered Entity?
The excluded benefits that would exempt a health plan from being a Covered Entity are listed in §300gg-91 of the Public Health Act (search for “benefits not subject to requirements”). This include, but are not limited to, workers´ compensation insurance, accident insurance that includes medical payment insurance, and automobile insurance in which benefits for medical care are included.
Why are On-Campus Health Centers Exempt from HIPAA?
On-campus health centers are exempted from HIPAA if they only provide medical services for students because students´ medical records are considered to be part of their educational records, which are protected by the Family Educational Rights and Privacy Act (FERPA). The HIPAA General Rules exclude records protected by FERPA from the definition of PHI, and an on-campus health center that only provides medical services for students cannot “transmit PHI in connection with a transaction for which a HIPAA standard exists” because it does not have any PHI.
In the event that an on-campus health center treats both students and members of the public, the health center becomes a “hybrid entity”. In such circumstances, students´ medical (educational) records are still subject to FERPA and must be isolated from other patients´ PHI – which is subject to the protections of the Privacy and Security Rules; and, in the event of a data breach, the processes of the Breach Notification Rule.
Why are paper-to-paper non-digital fax communications not considered electronic transmissions?
Paper-to-paper, non-digital fax communications are not considered electronic transmissions when the information being exchanged did not exist in electronic format prior to the fax transmission. If a healthcare provider only transmits health information for a HIPAA transaction by paper-to-paper non-digital fax, the healthcare provider is not a Covered Entity.
However, as well as paper-to-paper faxes being a poor data security practice, if the faxed health information was stored electronically prior to transmission (i.e., saved on a workstation) or any other electronic communication channel is used for any other HIPAA transaction, the healthcare provider is a Covered Entity, and all transmissions are subject to HIPAA compliance requirements.
Why Might Only Some of the Administrative Simplification Provisions Apply to Covered Entities?
Some of the Administrative Simplification provisions will not apply to Covered Entities due to the nature of the Covered Entities’ operations. For example, health care clearinghouses are typically business-to-business operations, so there will be no need to develop and distribute a Notice of Privacy Practices to individuals. Similarly, sole medical practitioners will not have to develop and distribute a workforce sanctions policy.
Another example is the “flexibility of approach” clause in the Security Rule (§164.306) which allows Covered Entities and Business Associates to be flexible about what security measures are adopted according to their size, complexity and capabilities, the costs of the security measure, and the probability and criticality of risks to PHI. However, the decision not to apply a Security Rule standard has to be justified, documented, and periodically reviewed to determine whether the decision is still justified.
When “Minimizing Risks to an Appropriate Level”, What is an Appropriate Level?
With regards to minimizing risks to an appropriate level, neither the Privacy Rule nor the Security Rule define what an “appropriate level” is – nor provide guidance on how an appropriate level can be obtained. In its HIPAA Basics Guide, CMS states “what’s reasonable and appropriate depends on your business as well as its size, complexity, and resources”. However, this statement should not be construed as an excuse to take shortcuts with HIPAA compliance or omit Administrative Simplification provisions.
How does a HIPAA Privacy Office Enforce an Organization’s HIPAA-Compliant Policies?
A HIPAA Privacy Officer can enforce an organization’s HIPAA-compliant policies in several ways. The primary tool in a Privacy Officer’s enforcement armory is the sanctions policy. This policy should stipulate the nature of punishments for HIPAA violations – which may range from a warning for minor violations to criminal proceedings and loss of license for serious violations. All members of an organization´s workforce should be provided with a copy of the sanctions policy regardless of whether they have access to PHI or not.
However, it is sometimes the case that a carrot rather than a stick is the best way to enforce an organization’s HIPAA-complaint policies, and Privacy Officers should focus on the benefits of compliance during HIPAA training. Naturally, the benefits will not be the same for all members of the workforce; but generally, HIPAA compliance leads to patients being more open about their conditions, which leads to better informed treatment programs and patient outcomes. This in turn improves staff morale and increases staff retention.
When might Individuals have an Opportunity to Agree or Object to a Disclosure of PHI?
Individuals have an opportunity to agree or object to a disclosure of PHI in several circumstances. Outside of the times when uses and disclosures of PHI fall into the categories of required, permissible, or requiring authorization, there are scenarios in which it is preferable, but not necessary, to obtain an individual´s “informal consent”. For example, notifying family members of a patient´s admission into hospital. In such scenarios, the individual should be given the opportunity to agree or object to the disclosure of PHI unless the individual is unable to, in which case Covered Entities are allowed to use their professional judgement.
Do Members of the Workforce Need to Report HIPAA Violations if they don’t Result in a Data Breach?
Members of the workforce should be required to report HIPAA violation if they don’t result in a data breach because, if violations are not identified and addressed, they could continue and contribute towards a culture of non-compliance which ultimately results in data breaches. Ideally, Covered Entities and Business Associates should implement a process for reporting HIPAA violations that allows members of the workforce to report violations anonymously.
What are the Breach Notification Rule requirements?
The Breach Notification Rule requirements vary depending on the type of organization at which a breach occurs. For example, Business Associates are required to notify Covered Entities of a breach, Covered Entities are required to notify affected individuals and HHS´ Office for Civil Rights of a breach, and organizations not covered by HIPAA are required to notify affected individuals and the FTC of a breach. State laws may also require breaches are notified to local authorities.
Because the Breach Notification Rule requirements vary, we have produced a comprehensive article explaining what organizations should do following a data breach. Alternatively, you can review the HIPAA Breach Notification standards at §164.400 of the Code of Federal Regulations.
Who enforces the Administrative Simplification requirements?
The Administrative Simplification requirements (Part 160, 162, and 164 of 45 CFR Subtitle A, Subchapter C), are enforced by two agencies within the Department of Health and Human Services – the Centers for Medicare and Medicaid Services (CMS) and the Office for Civil Rights (OCR).
Compliance with Part 162 – the Transaction Rules, Operating Rules, Code Set Rules, etc. – is enforced exclusively by CMS, while compliance with Part 164 – the General Rules, Privacy Rule, Security Rule, etc. – is enforced exclusively by OCR – unless a violation involves a criminal activity, in which case the violation is referred to the Department of Justice.
Who is required to follow HIPAA requirements?
The list of individuals and organizations required to follow HIPAA requirements is quite extensive. Generally, most health plans, health care clearinghouses, healthcare providers (including pharmacies), and Business Associates that provide a service for or on behalf of these organizations are required to follow the HIPAA requirements – but there are exceptions.
For example, insurance companies that provide health coverage as a secondary benefit to (say) auto insurance are not required to follow HIPAA requirements, nor are healthcare providers that do not conduct transactions for which HHS has developed standards (i.e., a counselling service that only accepts direct payments from clients).
In addition to the above, members of a Covered Entity’s or Business Associate’s workforce are required to follow whatever HIPAA requirements are included in workplace policies. Compliance with these requirements is often a condition of employment, and although a minor violation of HIPAA may not result in the termination of an employment contract, more serious violations likely will.
What is the importance of HIPAA compliance in healthcare?
The importance of HIPAA compliance in healthcare is that when healthcare providers demonstrate compliance with HIPAA, it increases patients’ trust that confidential information will remain private. Patients who believe confidential information will remain private are more prepared to share personal details of their physical and mental condition with a healthcare provider.
With more complete information, healthcare providers can make more accurate diagnoses and prescribe optimal courses of treatment. This results in better patient outcomes, which raises staff morale, increases staff retention, and improves the Overall Hospital Quality Star Rating – all of which can be financially beneficial to a HIPAA Covered Entity.
What is required for HIPAA compliance?
What is required for HIPAA compliance is an understanding of which HIPAA standards apply to your organization, the development of policies and procedures to enable compliance with the HIPAA standards, a comprehensive HIPAA training program, and a system of monitoring compliance – and reporting non-compliance – to prevent poor compliance practices developing into a cultural norm.
What is the key to success for HIPAA compliance?
The key to success for HIPAA compliance is asking for help when you need it. HIPAA consists of multiple sets of standards which do not apply to organizations in exactly the same way. If you are unsure about how to make your organization HIPAA compliant, it can be more cost-effective to pay for professional compliance help than to find out later you have made a costly mistake.
What is HIPAA compliance in healthcare?
HIPAA compliance in healthcare usually means complying with the standards of 45 CFR Parts 160,162, and 164 that apply to your organization. However, not all healthcare providers are required to comply with HIPAA, and if you are unsure about your HIPAA “status” you should seek professional advice from an expert with experience in HIPAA compliance.
What is a HIPAA compliance officer?
A HIPAA compliance officer is an individual tasked with responsibility for HIPAA compliance. The individual could be an existing employee or an outsourced expert, and could be responsible for compliance with the Privacy Rule, compliance with the Security Rule, or both. The individual will also be responsible for developing policies and procedures to comply with the Breach Notification Rule.
What is PCI HIPAA compliance?
There is no such thing as PCI HIPAA compliance. Organizations can be subject to both the Payment Card Industry Data Security Standard (PCI-DSS) and HIPAA compliance, but the two sets of standards protect different things. PCI-DSS protects the privacy and security of cardholder data, while HIPAA protects the privacy and security of individually identifiable health information.
What is HIPAA compliance training?
HIPAA compliance training can be either the training provided by an employer to members of the workforce to comply with the HIPAA training requirements, or training provided by a third party training organization. Often, the training provided by a third party organization is foundation training in HIPAA compliance so that employers can provide policy and procedure training without having to explain what HIPAA is and basics such as what Protected Health Information consists of.
What is HIPAA compliance certification?
HIPAA compliance certification is a point-in-time certification that an organization, individual, or software solution is considered HIPAA compliant. Although no particular HIPAA compliance certification is endorsed by HHS Office for Civil Rights, being certified demonstrates a good faith effort to comply with the applicable standards of the Administrative Simplification Regulations.
What is HIPAA and HITECH compliance?
HIPAA and HITECH compliance is a bit of a misnomer because most of the provisions of HITECH that impact HIPAA compliance were integrated into HIPAA via the Omnibus Final Rule of 2013. If an individual or organization complies with the applicable standards of HIPAA, they automatically comply with the applicable provisions of HITECH.
What is needed for HIPAA compliance for electronic claims?
What is needed for HIPAA compliance for electronic claims depends on the HIPAA status of the organization processing electronic claims. If the organization is a Covered Entity that processes electronic claims in-house, it is necessary to comply with all applicable standards of the Administrative Simplification Regulations (including Part 162 standards).
If the organization is a Business Associate processing electronic claims on behalf of a Covered Entity, it is necessary to comply with the standards in Part 162, the Security Rule, and the Breach Notification Rule – along with any Privacy Rule standards stipulated in a Business Associate Agreement – a Business Associate Agreement also being necessary to comply with HIPAA.
What is a HIPAA compliance privacy officer?
A HIPAA compliance privacy officer is an individual tasked with responsibility for an organization’s compliance with the HIPAA Privacy Rule. The individual is also a point of contact for patients, members of the workforce, and HHS’ Office for Civil Rights who have questions about an organization’s compliance or who want to report or investigate a HIPAA violation.
The individual can be a member of a Covered Entity’s workforce or an outside entity contracted to the role on a temporary or permanent basis. In smaller organizations, the HIPAA compliance privacy officer may also double up as the security officer – in which case, they also have responsibility for an organization’s compliance with the HIPAA Security and Breach Notification Rules.
What is a BAA in HIPAA compliance?
A BAA in HIPAA compliance is a Business Associate Agreement between a Covered Entity and a Business Associate. The Agreement stipulates the terms under which the Covered Entity will share PHI with a Business Associate and what the responsibilities of each party are. It is important to be aware that BAAs are also necessary when a Covered Entity is providing a service for or on behalf of another Covered Entity when there is no existing direct treatment relationship with a patient.
What is the first step you would take when creating a HIPAA compliance plan?
The first step you would take when creating a HIPAA compliance plan is to establish which of the HIPAA standards are applicable to your organization’s activities. This is particularly important when an organization qualifies as a hybrid entity and some activities covered by HIPAA need to be isolated from activities not covered by HIPAA.
What is a HIPAA compliance audit?
A HIPAA compliance audit can be one of two things. It can either be an audit conducted by HHS’ Office for Civil Rights as part of the agency’s audit program or as part of an investigation into a data breach. Alternatively, a HIPAA compliance audit can be an audit of an organization’s compliance program – either done in-house or by an external compliance specialist.
What is the first step to get started with HIPAA compliance?
The first step to get started with HIPAA compliance is to designate the roles of Privacy and Security Officers. These individuals are responsible for HIPAA compliance within an organization so should be involved at the very start to help identify which HIPAA standards apply to the organization and what measure, policies, and procedures are required to fulfill the organization’s compliance obligations.
What government agency is responsible for supervising HIPAA compliance?
The government agency responsible for supervising HIPAA compliance is the Department of Health and Human Services (HHS). Within the Department, the Office for Civil Rights (OCR) is responsible for supervising compliance with Parts 160 and 164 of the Administrative Simplification Regulations, while the Centers for Medicare and Medicaid Services (CMS) is responsible for supervising Part 162.
What is a HIPAA compliance assessment?
A HIPAA compliance assessment is similar to an internal HIPAA compliance audit inasmuch as the objective of the assessment is to assess the level of compliance within an organization, identify gaps in compliance, and determine appropriate measures to fill the gaps. Like a HIPAA compliance audit, a HIPAA compliance assessment can assess an organization’s compliance program as a whole, or individual elements of the HIPAA compliance program.
What is the compliance deadline for the HIPAA Act of 1996?
The compliance deadline for the HIPAA Act of 1996 varies depending on which part of the Act you look at. It is important to remember that the HIPAA Act covered many subjects in addition to the privacy and security of individually identifiable health information, and some deadlines were retrospective, some were immediate, and others took many years to become effective.
What are the possible consequences of HIPAA non-compliance?
The possible consequences of HIPAA non-compliance vary according to the nature of the violation and its impact. Most minor violations are resolved by verbal warnings and additional training. However, major violations can result in multi-million dollar fines for Covered Entities and – for individuals who do not comply with HIPAA – a fine of up to $250,000 and up to ten years in jail.
What is a medical assistant’s role in HIPAA compliance?
A medical assistant’s role in HIPAA compliance is the same as any other member of the workforce. As a medical assistant will have access to PHI, they should receive training on what PHI is, how it can permissibly be used or disclosed, and what the procedures are for obtaining consent, authorization, or attestation for other uses and disclosures. As with every other member of the workforce, a medical assistant should also receive security and awareness training.
What is the first step you should take when creating a HIPAA compliance plan?
The first step you should take when creating a HIPAA compliance plan is to establish which of the HIPAA Administrative Simplification Regulations apply to your organization. Most HIPAA-regulated entities will not be required to comply with every standard or implementation specification – although it is important not to overlook the General Rules at the start of each Part and Subpart.
What is the annual cost of HIPAA compliance?
There is no fixed annual cost of HIPAA compliance because the cost of complying with HIPAA can vary according to the type of organization and the nature of its activities. Other factors that can impact the annual cost of HIPAA compliance include the size of the workforce, how much technology the organization uses, and how much of the technology is already configured to be HIPAA compliant.
What is PHI in HIPAA compliance?
PHI in HIPAA compliance stands for Protected Health Information – individually identifiable health information that is protected by the standards of the Privacy and Security Rules. Because HIPAA compliance depends on understanding what uses and disclosures of Protected Health Information are permitted, it is important that Covered Entities, Business Associates, and members of their workforces fully understand what is considered PHI under HIPAA.
What is new for HIPAA compliance?
What is new for HIPAA compliance depends on which area of HIPAA the question relates to. There have been multiple changes to the Part 162 regulations in recent years, but not so many changes to the Privacy, Security, and Breach Notification Rules. However, compliance with these Rules can be impacted by changes to other regulations; and Covered Entities and Business Associates should keep up to date with changes to 42 CFR Part 2, CMS’ Interoperability Rule, and HITECH.
What is HIPAA compliance and how to improve it?
HIPAA compliance means complying with the applicable regulations, standards, and implementation specifications of the HIPAA Administrative Simplification Regulations (45 CFR Parts 160, 162, and 164). In order to determine how you can improve HIPAA compliance, you first have to determine which standards apply to your organization and which of these standards are not being complied with. Only then can you develop policies and procedures to improve HIPAA compliance.
How does the government define a workforce for the purposes of HIPAA compliance?
The government defines a workforce for the purposes of HIPAA compliance as “employees, volunteers, trainees, and other persons whose conduct, in the performance of work for a covered entity or business associate, is under the direct control of such covered entity or business associate, whether or not they are paid by the covered entity or business associate.” (45 CFR §160.103).
Which agency is responsible for enforcing HIPAA compliance?
The agency responsible for enforcing HIPAA compliance is the Department of Health and Human Services (HHS). Within the Department, the Office for Civil Rights (OCR) is responsible for enforcing compliance with Parts 160 and 164 of HIPAA, while the Centers for Medicare and Medicaid Services (CMS) is responsible for enforcing compliance with Part 162 of HIPAA.
Why is HIPAA compliance important?
HIPAA compliance is important because compliant organizations protect the privacy of individually identifiable health information and ensure the confidentiality, integrity, and availability of electronic Protected Health Information while facilitating the flow of information to support a more efficient healthcare service.
When patients trust their sensitive health information is protected, they tend to be more open about their conditions, their symptoms, and their concerns. With more information to work with, healthcare providers can make better informed decisions about diagnoses and treatment plans – resulting in better patient outcomes.
Better patient outcomes raise staff morale and increase staff retention rates. Better patient outcomes also reflect well in HCAHPS surveys. For these reasons alone, it is in everybody’s best interests for Covered Entities and Business Associates to comply with HIPAA, train the workforce on HIPAA compliance, and monitor compliance at all times.
What is HIPAA compliance in healthcare?
HIPAA compliance in healthcare means complying with the applicable regulations, standards, and implementation specifications of the HIPAA Privacy, Security, and Breach Notification Rules; and, if not subcontracted out, the Administrative Requirements of HIPAA Part 162. Although healthcare organizations are most often responsible for HIPAA compliance, healthcare professionals will find it beneficial to comply with HIPAA as this article explains.
HIPAA compliance records must be retained for how many years?
HIPAA compliance records must be retained for a minimum of six years from the date on which the record was last in effect. For example, if an employee attested to undergoing HIPAA training in 2019, the record must be retained until at least 2025. However, if a HIPAA compliance record relates to a policy created in 2019 which is still in force, the record must be retained for at least six years from the date the policy is no longer in force.
When does HIPAA require compliance with the data breach notification rules?
HIPAA requires compliance with the breach notification rules when there is an impermissible use or disclosure of unsecured Protected Health Information which compromises the security or privacy of the Protected Health Information. In such cases Covered Entities – and Business Associates when necessary – must follow the procedures in 45 CFR Part 164 Subpart D.
Who oversees HIPAA compliance?
Who oversees HIPAA compliance depends on the context. For example, a Privacy Officer oversees workforce compliance with the Privacy Rule, a Covered Entity oversees Business Associate compliance, HHS’ Office for Civil Rights oversees compliance with the Privacy, Security, and Breach Notification Rules, and the Centers for Medicare and Medicaid Services oversees compliance with the Part 162 Administrative Regulations.
Which method of sending mail is considered the most secure to maintain compliance with HIPAA?
The method of sending mail considered the most secure to maintain compliance with HIPAA is any technology that has the required safeguards to comply with the Security Rule. When using a secure service to communicate Protected Health Information, it is also necessary to enter into a Business Associate Agreement with the service vendor, and important that the patient has not objected to the use of the service or requested communications via an alternative method.
Who needs HIPAA compliance?
Organizations that need HIPAA compliance are those who qualify as Covered Entities under HIPAA, Business Associates of Covered Entities, and subcontractors of Business Associates. It is also important that members of each organization’s workforce are trained in HIPAA compliance in relation to their roles within the organization.
What is required for HIPAA compliance?
What is required for HIPAA compliance is an understanding of the HIPAA Administrative Simplification Regulations. This will help organizations determine which standards apply to their activities, develop policies and procedures so the activities are conducted in compliance with HIPAA, and train members of the workforce on the policies and procedures.
It is also necessary for HIPAA compliance to have an understanding of network systems, know how to configure software to comply with Security Rule standards, and provide security and awareness training to all members of the workforce. Finally, all organizations must have a sanctions policy for members of the workforce who fail to comply with the HIPAA policies and procedures.
What are the penalties for HIPAA non-compliance?
The penalties for HIPAA non-compliance depend on the non-compliant party. If a member of the workforce violates HIPAA, the penalty will depend on the nature of the violation, the consequences, and the content of the employer’s sanctions policy. In most cases, the penalty will be a verbal or written warning accompanied by additional training except for in serious or repeated cases.
If a Covered Entity or Business Associate violates HIPAA, the penalties are more likely to be financial – even if they do not consist of civil monetary penalties. In the majority of cases, corporate penalties for HIPAA non-compliance consist of corrective action plans – some of which can last for two years and incur significant indirect costs due to the requirements of the corrective action plan.
What is the importance of HIPAA compliance in healthcare?
The importance of HIPAA compliance in healthcare is that complying with HIPAA protects the privacy of individually identifiable health information. When patients trust their confidential health information will remain confidential, they tend to be more forthcoming about the symptoms of their illnesses and the consequences of their injuries.
With more complete information, healthcare professionals can make better inform diagnoses and prescribe more effective treatment plans. This results in better patient outcomes, which benefits hospitals financially due to fewer readmissions, raises staff morale, and improves staff retention rates – further benefiting hospitals financially.
How can you maintain HIPAA compliance?
You can maintain HIPAA compliance by providing refresher HIPAA training to all members of the workforce. HIPAA only requires Privacy Rule training at the start of employment and when a material change to policies occurs. This can leave significant gaps between training sessions for some members of the workforce – during which time compliance shortcuts can become commonplace and develop into a culture of non-compliance.
Who enforces HIPAA compliance?
Who enforces HIPAA compliance depends on the context. Within an organization, a HIPAA Privacy Officer most often enforces HIPAA compliance. The agencies that enforce HIPAA compliance on organizations are the Office for Civil Rights and the Centers for Medicare and Medicaid Services – unless an organization does not qualify as a Covered Entity or Business Associate, in which case compliance with the Breach Notification Rule is enforced by the Federal Trade Commission.
Why are policies and procedures an important part of HIPAA Privacy Rule compliance?
Policies and procedures are an important part of HIPAA Privacy Rule compliance because policies define when members of the workforce can use or disclose Protected Health Information (PHI), while policies define how members of the workforce can use or disclose PHI. Procedures can also define how members of the workforce should respond to a patient exercising their Privacy Rule rights.
What are the compliance deadlines for the HIPAA regulations?
The compliance deadlines for the HIPAA regulations vary. At the time HIPAA was passed, some regulations were enacted retrospectively, while others took effect on the day the Act was signed into law. The compliance deadline for the first of the Administrative Simplification regulations – the HIPAA standards for electronic transactions and code sets – was October 2002. Later compliance deadlines include:
- April 2003 – Compliance deadline for the Privacy Rule
- April 2005 – Compliance deadline for the Security Rule
- September 2009 – Compliance deadline for the Breach Notification Rule
- September 2013 – Compliance deadline for the Final Omnibus Rule
Who has the authority to enforce HIPAA compliance?
The authority to enforce HIPAA compliance within an organization is most often the Privacy Officer or – if the organization qualifies as a Business Associate – the Security Officer. Organizations can also be subject to enforcement action by HHS’ Office for Civil Rights (for violations of HIPAA Parts 160 and 164) or by the Centers for Medicare and Medicaid Services (for violations of HIPAA Part 162).
What are the fines associated with violating the HIPAA compliance requirements?
The fines associated with violating the HIPAA compliance requirements vary according to the degree of culpability. The following list represents the fines that can be issued by HHS’ Office for Civil Rights for violating the HIPAA compliance requirements.
- If a violation is attributable to a lack of knowledge, fines range from $137 to $34,464 per violation.
- If a violation is attributable to a lack of care, fines range from $1,379 to $68,928 per violation.
- If a violation is attributable to willful neglect, fines range from $13,785 to $68,928 per violation.
- If a violation is attributable to willful neglect and not corrected within 30 days, the maximum fine of $68,928 applies.
Fines for violating the HIPAA compliance requirements can also be issued by State Attorneys General; and, if a violation results in the wrongful disclosure of individually identifiable health information for personal gain, competitive advantage, or malicious intent, individuals can also be fined up to $250,000 by the Department of Justice.
Who monitors HIPAA compliance?
Who monitors HIPAA compliance depends on the circumstances. Within an organization, HIPAA compliance is monitored by a Privacy and/or a Security Office – although in a large organization, HIPAA compliance is more likely monitored on the ground by team supervisors and line managers who report to a compliance team.
It is not the case that HHS’ Office for Civil Rights monitors HIPAA compliance. HHS’ Office for Civil Rights only hears about HIPAA violations when it receives a complaint or a report of a data breach. Although the agency will review HIPAA compliance as part of an investigation into a complaint, it is not responsible for monitoring compliance with HIPAA.
Who audits HIPAA compliance?
Audits of HIPAA compliance can be conducted internally, by a third party compliance organization, or by HHS’ Office for Civil Rights during the course of an investigation. Several years ago, HHS’ Office for Civil Rights launched a HIPAA audit program, but this was never continued after the second phase of audits in 2016.
How can you improve HIPAA compliance?
You can improve HIPAA compliance by auditing your existing policies and procedures to identify any gaps in compliance. If gaps exist, you may need to revise existing policies and procedures or create new policies and procedures. If the revised or new policies and procedures result in a material change to HIPAA compliant working practices, it will also be necessary to train affected members of the workforce.
What are the penalties for non-compliance with HIPAA?
The penalties for non-compliance with HIPAA depend on who is not complying. If a member of the workforce is not complying with their employer’s HIPAA policies and procedures, the penalties for non-compliance with HIPAA will be stipulated in the employer’s sanctions policy. These usually consist of a verbal or written warning and additional training.
If an organization that qualifies as a HIPAA Covered Entity or Business Associate fails to comply with HIPAA, the penalty will depend on the nature of the non-compliant event and its consequences. In most cases, the penalty for non-compliance with HIPAA is voluntary compliance or a corrective action plan. In severe cases of non-compliance, the penalties may be financial.
What are the implications of non-compliance with HIPAA?
The implications of non-compliance with HIPAA depend on whether you are a member of an organization’ s workforce or an organization subject to the HIPAA Rules. If the former, the implications of non-compliance with HIPAA will range from additional training to a written warning or loss of employment for severe or repeated violations.
If an organization fails to comply with HIPAA, the likely implication is that it will be required to adopt voluntary compliance measures or complete a corrective action plan. Only in serious cases of non-compliance will an organization be issued with a civil monetary penalty – the amount of the penalty varying according to the organization’s degree of culpability.
What are the three phases of HIPAA compliance?
The three phases of HIPAA compliance are often referred to as the three Rules of HIPAA (Privacy, Security, and Breach Notification) or the three safeguards of the Security Rule (Administrative, Physical, and technical). None of these terms is accurate as HIPAA compliance should be an ongoing program (i.e., unlimited phases), there are more than three Rules of HIPAA (and it is important all organizations are familiar with the General Rule); and, although there are only three safeguards in the Security Rule, they should not be taken out of context with the rest of the Security Rule.
How much does HIPAA compliance cost?
How much HIPAA compliance costs is relative to the size of an organization, the nature of its activities, and the existing measures and technologies it has in place that could be refactored to support HIPAA compliance. Staff knowledge is also an important factor as it will cost less to train a workforce already familiar with general compliance and security best practices than it will to train a workforce from scratch.
What does HIPAA compliance mean for chat messaging?
What HIPAA compliance means for chat messaging is that any messaging between healthcare professionals that involves a use or disclosure of PHI should be for a permissible use or disclosure of PHI, the communication should be conducted over a secure communication channel (i.e., not SMS), and the PHI disclosed in the communication should be limited to the minimum necessary.
With regards to chat messaging between a healthcare and a patient, if the communication is not conducted over a secure channel (i.e., initiated by the patient), the patient should be alerted to the risks of disclosing PHI. If the patient decides to continue with the chat, both the warning and the patient’s consent to continue should be documented and retained.
Which part of HIPAA specifies the consequences for non-compliance?
The part of HIPAA that specifies the consequences of non-compliance is the Enforcement Rule which can be found in 45 CFR Part 160 Subparts C, D, and E. The amounts of the civil monetary penalties have since been amended by the HITECH Act, and – since 201 – adjusted annually for inflation. The current financial penalties for non-compliance with HIPAA can be found in this article.
What should employees know about HIPAA compliance?
What employees should know about HIPAA compliance goes beyond the HIPAA training requirements of the Privacy and Security Rules. Ideally, employees should know a little about why HIPAA exists, what is considered PHI under HIPAA, and why compliance with HIPAA is important – especially in terms of the benefits to patients.
Which government agency regulates compliance with and enforces HIPAA?
Various government agencies regulate compliance with and enforce HIPAA because HIPAA covers much more than the privacy and security of PHI. For example, the Department of Labor regulates compliance and enforces the provisions of HIPAA relating to the portability, access, and renewability requirements for group health plans. The Department of the Treasury and the Federal Trade Commission also play roles in the regulation and enforcement of HIPAA.
With regards to the section of HIPAA relating to the privacy and security of PHI, the government agency that regulates compliance with and enforces this part of HIPAA is the Department of Health and Human Services. Within the Department, the agency that enforces Parts 160 and 164 of HIPAA (which includes the Privacy, Security, and Breach Notification Rules) is the Office for Civil Rights. Part 162 of HIPAA (mostly Code Sets and Transaction Rules) is regulated by CMS.
How long must HIPAA compliance records be retained?
HIPAA compliance records must be retained for a minimum of six years if the records document events relating to HIPAA compliance – for example, risk assessments and records of workforce training. It is important to note that the six year retention period starts when a document is no longer in used. For example, if Notice of Privacy Practices v1 was replaced by Notice of Privacy Practices v2 in 2020, a copy of version 1 will have to be retained until at least 2026.
How should you audit business associates for HIPAA compliance?
You should audit business associates for HIPAA compliance by first asking for a copy of compliance or security certifications they have achieved. If the business associate has a standard BAA (companies like Microsoft, Google, IBM, etc. only enter into their own BAAs), you should also ask for a copy of this too in order to ensure you agree with the terms of the BAA and understand your responsibilities.
These documents should satisfy the HIPAA requirements to conduct due diligence on business associates. However, if the due diligence raises concerns that a potential business associate is not fully compliant with HIPAA, it may be better to source a different business associate than going to the expense of a full audit – only to find the potential business associate is unwilling or unable to resolve the issues found in the audit.
How does HIPAA compliance affect healthcare facilities?
HIPAA compliance affects how healthcare facilities respect the privacy and security of patients’ health information and what access patients are given to their health information to make better informed decisions about healthcare providers. Being HIPAA compliant can benefit healthcare facilities due to a more trusting relationship between patients and the facility, which can result in better patient outcomes, higher staff morale, and lower readmission rates.
What is the compliance date for the HIPAA Privacy Rule?
The compliance date for the HIPAA Privacy Rule was originally February 26, 2001. However, due to tens of thousands of comments raising concerns about the complexity of the Rule, the compliance date for the HIPAA Privacy Rule was delayed for most covered entities to April 14, 2003. Subsequent amendments to the Privacy Rule also have their own compliance dates. For example, the changes to the Privacy Rule in the HIPAA Final Omnibus Rule had a compliance date of September 23, 2013.
What policies and procedures are necessary for compliance with the HIPAA Security Rule?
The policies and procedures necessary for compliance with the HIPAA Security Rule are those which relate to any applicable standard or implementation specification in 45 CFR Part 164, Subpart C. Because HIPAA is technology neutral, because not all standards will apply to all organizations, and because of the Security Rule’s “flexibility of approach” it is impossible to create a definitive one-size-fits-all list of the policies and procedures that are necessary for compliance with the Security Rule.
How does HIPAA compliance affect healthcare providers?
HIPAA compliance affects healthcare providers by making healthcare professionals more conscious of when it is permissible to disclose health information. Depending on who disclosures are made to, HIPAA compliance can also affect how much health information healthcare providers will disclose (because of the minimum necessary standard) and whether the patient’s consent or authorization is sought before any disclosure is made at all.
Who do you report HIPAA non-compliance to?
Who you report HIPAA non-compliance to varies depending on whether you are a member of a Covered Entity’s or Business Associate’s workforce or an individual. If you are a member of the workforce, who you report HIPAA non-compliance to may be stipulated in your employment contract or during HIPAA training. Usually, it would be an immediate supervisor, but your employer may have implemented an anonymous tip service to encourage reports in difficult circumstances.
Individuals have the choice of reporting HIPAA non-compliance to an organization’s Privacy Officer, the State Attorney General, or HHS’ Office for Civil Rights. In most cases, State Attorneys general will not investigate a complaint relating to non-compliance unless a complaint has also been made to HHS’ Office for Civil Rights. Members of a workforce can also report HIPAA non-compliance to HHS’ Office for Civil Rights if their internal report fails to resolve the non-compliance issue.
What are the essential parts of a successful HIPAA security compliance program?
The essential parts of a successful HIPAA security compliance program are compliance analyses, policy development, and workforce training. Without these three parts, it is impossible to identify gaps in security compliance, resolve the gaps, and ensure the workforce is trained to use whichever resolutions are introduced in compliance with HIPAA. It is important to note that these three parts of a successful HIPAA security compliance program are ongoing rather than one-off events.
What must I say in my phone answering message for HIPAA compliance?
It is not what you must say in your phone answering message for HIPAA compliance, but what you must not say. Unless a patient has given their consent for you to leave messages including sensitive information, you should avoid disclosing PHI in all answering device messages because you have no control over who will hear the information or that they will not further disclose it without the patient’s authorization. To be sure of complying with HIPAA, it is a best practice to avoid disclosing PHI in any message.
What does HIPAA compliant cloud provider mean?
HIPAA compliant cloud provider means the cloud provider has implemented the measures required to provide a cloud service in compliance with HIPAA and will enter into a Business Associate Agreement with a Covered Entity or upline Business Associate. It is important to be aware that a “HIPAA compliant anything” does not guarantee HIPAA compliance, as compliance with HIPAA is determined by how the cloud service is configured and used rather than by the service’s capabilities.
Who should be included on a hospital HIPAA compliance committee?
Representatives should be included on a hospital HIPAA compliance committee from every department and from every subcontracted service to ensure the hospital’s HIPAA compliance policies are applied standardly throughout the hospital. Ideally, in addition to HR, legal, and IT, a hospital HIPAA compliance committee should include representatives from nursing, security, environmental services, and administration at a minimum.
When did HIPAA compliance have to be in place?
For some organizations, HIPAA compliance had to be in place as early as October 2002 as this was the first compliance date for electronic transactions and code sets. HIPAA compliance with the Privacy Rule had to be in place in April 2003, while the compliance deadline for the HIPAA Security Rule was April 2005. Subsequent compliance dates include September 2009 (the Breach Notification Rule) and September 2013 (the HIPPA Final Omnibus Rule).
What does a HIPAA compliance officer do?
A HIPAA compliance officer oversees an organization’s compliance efforts. The officer is responsible for ensuring policies and procedures are developed that comply with the applicable standards of HIPAA, that training is provided to all members of the workforce, that compliance is monitored, and that non-compliance is sanctioned.
The HIPAA compliance officer is also the point of contact for patients and members of the workforce who have complaints or queries, and the point of contact for HHS’ Office for Civil Rights in the event that a complaint is escalated or a data breach is reported to the agency.
When it comes to HIPAA compliance, what is the difference between a policy and a procedure?
When it comes to HIPAA compliance the difference between a policy and a procedure is that a policy is a documented requirement, standard, or guideline, and a procedure explains the process for performing a task in compliance with the policy. An example in the context of HIPAA is a policy stating a hospital will not disclose Part 42 health information without an authorization, while the procedure explains how members of the workforce should acquire an authorization when necessary.
Where do you get HIPAA compliance training?
You can get HIPAA compliance training from two sources – your employer and third party training organizations. Generally, an employer will provide HIPAA compliance training relative the functions you perform, while a third party training organization will provide more general HIPAA compliance training to give you a better understanding of why HIPAA exists, what its purpose is, and how the standards of the HIPAA Rules enable HIPAA to achieve its purpose.
How do you investigate HIPAA compliance?
You would usually investigate HIPAA compliance after a complaint from a patient, a report from a member of the workforce, or a contact by HHS’ Office for Civil Rights. The nature of the complaint, report, or contact will determine the nature of the non-compliant event and how it should be investigated. It is important that when you investigate HIPAA compliance to keep an open mind. More than two-thirds of complaints to HHS’ Office for Civil Rights are rejected because no violation of HIPAA has occurred.
How has HIPAA changed and why is HIPAA compliance becoming more challenging?
HIPAA has changed in many ways since the publication of the first Administrative Simplification Regulations and HIPAA compliance has become more challenging because of these changes. Further proposed changes to HIPAA such as CMS’ Interoperability Rule, attested uses and disclosures, and Part 2 integration with the Privacy Rule will further increase the challenges to HIPAA compliance.
How is HIPAA compliance measured?
HIPAA compliance is measured by a lack of complaints from patients, internal violation reports, and contacts from HHS’ Office for Civil Rights. While this is not a foolproof method of measuring HIPAA compliance, a lack of complaints, reports, and contacts gives compliance officers more time to focus on gap analyses, workforce training, and compliance monitoring.
HIPAA Resources
Further information about HIPAA requirements that coudld help with the compilation of a HIPAA compliance checklist can be found throughout the HIPAAJournal.com website. However, in order to assist organizations looking for quick answers to complex questions, we have listed a selection of HIPAA compliance resources below.
General HIPAA Guidance
What is protected health information?
What is “HIPAA Certification”?
The Most Common HIPAA Violations You Should Be Aware Of



 HIPAA Privacy Rule
HIPAA Privacy Rule Organizational Requirements
Organizational Requirements






